PART A - ORDER OF BATTLE DATA BASE
Development of a detailed threat OB data base is vital to threat evaluation.
A
current and accurate data base on the enemy or potential enemy simplifies
evaluation of his doctrine and capabilities.
Review of the mission and battlefield area will help to identify and isolate threat
forces that threaten accomplishment of the mission.
After the threat is identified, information required for evaluation is assembled.
The primary sources of this information include:
* OB books and handbooks.
* Area handbooks and studies.
* Higher headquarters analysis, estimates, IPB products, and reports.
* Open source literature.
By carefully evaluating what is known and making reasonable judgments about what is
not known, you find information gaps. Information requirements are fed to the
collection management and dissemination (CM&D) section for processing into specific
orders and requests (SOR), and specific information requirements (SIR).
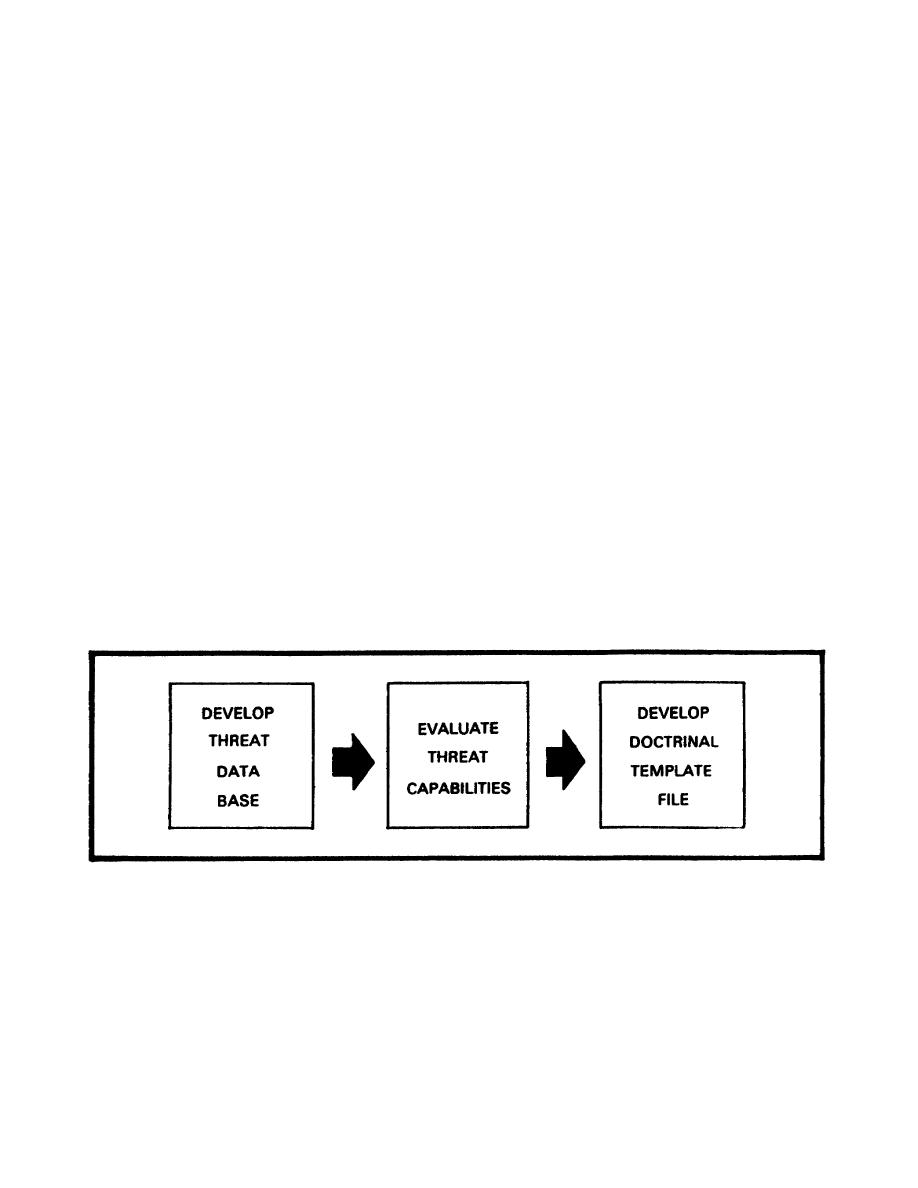
Information collected from SOR/SIR helps the commander determine the enemy's threat
capabilities
(Figure 4-1).
The threat capabilities are evaluated as they relate to the mission and the
battlefield area, and include evaluation of HVTs and rates of movement. Threat
evaluation follows the process as outlined below:
Figure 4-1.
Threat Evaluation Process.
IT 0462
4-2



 Previous Page
Previous Page
